45 aws best practices
AWS Security Best Practices - AWS Security Best Practices AWS Security Best Practices. AWS Whitepaper. Welcome; AWS Documentation AWS Whitepapers AWS Whitepaper. AWS Security Best Practices. PDF RSS. Notice: This whitepaper has been archived. For the latest technical information on ... AWS VPC Security: 13 Best Practices [The 2022 Guide] - Hyperglance The best practice is to split your production, staging, and pre-production environments across different VPCs. Image courtesy of AWS 5. Use Security Groups To Control Resource Access It's vital that you factor in AWS Identity Access Management (IAM) when you're planning and setting up your VPC.
5 AWS Monitoring Best Practices You Must Know - NetApp What are AWS Monitoring Best Practices? AWS monitoring best practices were developed to help you ensure that your resources and applications are operating efficiently, your costs are optimized, and your data remains secure. These practices incorporate a range of tools and techniques to grant you real-time, continuous visibility into your operations.

Aws best practices
PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 2 Know the AWS Shared Responsibility Model Amazon Web Services provides a secure global infrastructure and services in the cloud. You can build your systems using AWS as the foundation, and architect an ISMS that takes advantage of AWS features. Best practices for setting up Amazon Macie with AWS Organizations In this post, we'll walk through the best practices to implement before you enable Amazon Macie across all of your AWS accounts within AWS Organizations.. Amazon Macie is a data classification and data protection service that uses machine learning and pattern matching to help secure your critical data in AWS. To do this, Macie first automatically provides an inventory of Amazon Simple ... 21 Best Practices for AWS Cloud Security - Towards Data Science Best Practices for AWS Cloud Security 1. Put your strategy first and determine if it supports various tools and controls. There's a lot of debate around whether you should put tools and controls in place first, or set up the security strategy. While it might seem like an underlying discussion, the answer is more complex.
Aws best practices. AWS Best Practices for E-commerce - logicata.com AWS security best practices Keeping all your AWS resources inside a properly configured Virtual Private Cloud (VPC) will stop them from being publicly accessible over the internet. It is still possible to have a VPC and make specific resources publicly available - but you need to take care to ensure only the required traffic is exposed. AWS Security Group: Best Practices & Instructions - CoreStack Here are six best practices to assist in that process. Avoid the use of the "default" security group The "default" security group should not be used for active resources. This is because new AWS resources could be inadvertently assigned to it and thus allowed inappropriate access to confidential material. AWS Tagging - Strategy & Best Practices [The 2022 Guide] - Hyperglance AWS Tagging Best Practices The recipe for a great tagging strategy is no secret. Here are the ingredients: 1. Plan Your Tag List Nail this stage and everything after becomes easier. Realistically, in most organizations, you'll have stakeholders with requirements from a cross-section of teams. 10 AWS Security Best Practices For Developers | YourTechDiet Here are the 10 AWS Security Best Practices for Developers. Enable AWS CloudTrail; AWS CloudTrail is a tool that allows you to record API logs for security analysis, compliance auditing, and change tracking. With it, one can create trails of breadcrumbs which lead back to the source of any changes made to your AWS environment.
Follow best practices | AWS Quick Starts - GitHub Pages If you're implementing Lambda-backed custom resources in your CloudFormation stack, review the best practices discussed in the AWS Support Knowledge Center. Linux Enable the -e flag at the top of all scripts (except user data) as follows: #!/bin/bash -e This will cause the script to exit with a non-zero exit code. AWS Best Practices for Beginners - Career Karma AWS Best Practices and Guidelines FAQ What are the six pillars of AWS? The six pillars of AWS are sustainability, cost optimization, performance efficiency, reliability, security, and operational excellence. These pillars describe the concepts, principles, and best practices used in designing by architects to onset workloads on the cloud. Home - EKS Best Practices Guides - GitHub Pages Amazon EKS Best Practices Guide for Security¶ This guide provides advice about protecting information, systems, and assets that are reliant on EKS while delivering business value through risk assessments and mitigation strategies. The guidance herein is part of a series of best practices guides that AWS is publishing to help customers ... AWS Security Best Practices for Developers (2018) Security matters to everyone, but solid security practices start with the developer of an application. In this developer-centered course, instructor and AWS Certified Solutions Architect Carlos Rivas shows how to build stronger, more secure applications for deployment on Amazon Web Services.
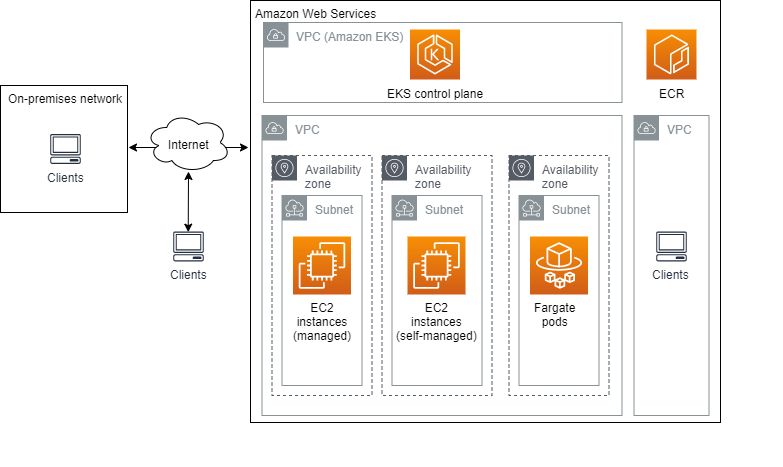
AWS best practices: Amazon Elastic Compute Cloud - Site24x7 AWS best practices for EC2 instances. Though EC2 boasts built-in security and better control over servers as the infrastructure scales, it becomes laborious to manage the complete fleet of resources in AWS infrastructure. To obtain the maximum benefit and fulfill the requirements of your target workloads, let's check out the best practices for ... AWS Cloud Security: The Best Practices - linkedin.com Here are some best practices to enable you ways to travel about it. Strategize: While the endeavors to achieve top-notch AWS cloud security are surely appreciable and advised, any attempt to ... Architecting for the loud Amazon Web Services – Architecting for the Cloud: AWS Best Practices Page 1 Introduction Migrating applications to AWS, even without significant changes (an approach known as lift and shift), provides organizations with the benefits of a secure and cost-efficient infrastructure. However, to make the most of the elasticity and agility that are ... Best practices for AWS Organizations - AWS Organizations Best practices for AWS Organizations - AWS Organizations AWS Documentation AWS Organizations User Guide Best practices for AWS Organizations PDF RSS We recommend that you follow these best practices when you create and operate your organization. Topics Best practices for the management account Best practices for member accounts
Best Practices for Organizational Units with AWS Organizations 21.07.2020 · The basis of a well-architected multi-account AWS environment is AWS Organizations, an AWS service that enables you to centrally manage and govern multiple accounts. This post dives deep into the recommended architecture of AWS best practices when building your organization. It will explain and illustrate the recommended OU structure and ...
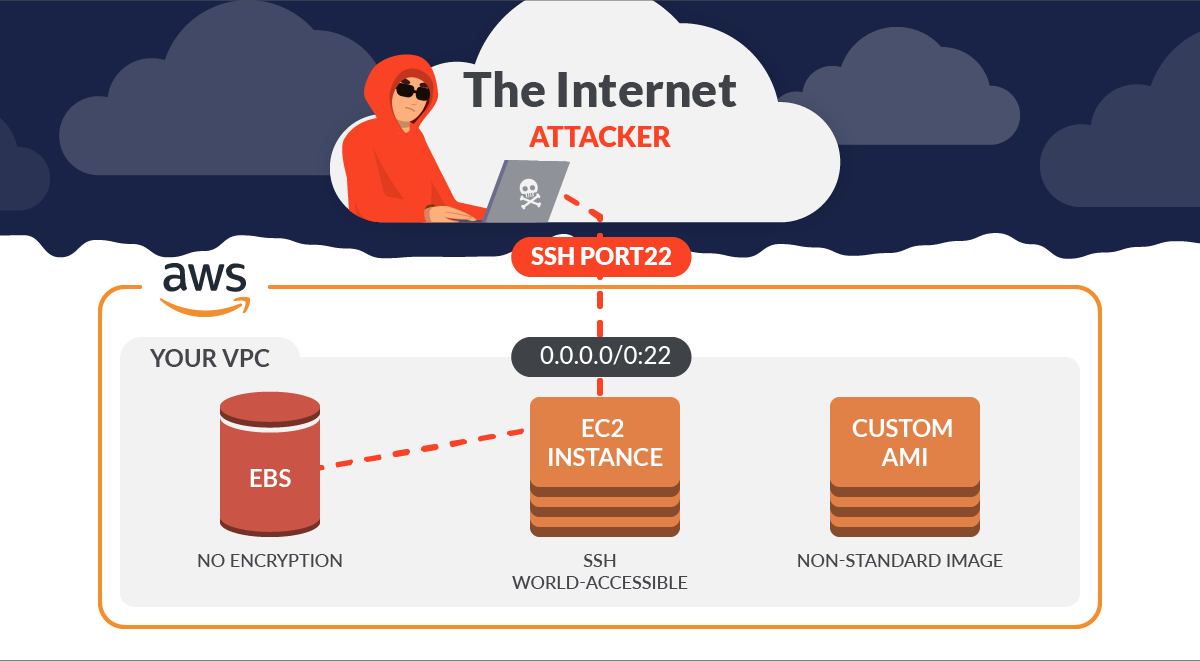
51 AWS Security Best Practices | McAfee Blog Below are some best practices around AWS database and data storage security: Ensure that no S3 Buckets are publicly readable/writeable unless required by the business. Turn on Redshift audit logging in order to support auditing and post-incident forensic investigations for a given database. Encrypt data stored in EBS as an added layer of security.
Establishing your best practice AWS environment The framework described on this page represents AWS best practices that you should use as a starting point for your AWS journey. To get started, refer to the AWS Organizations Getting Started Guide to build your own multi-account AWS environment. Alternatively, you can use AWS Control Tower to help you quickly set up a secure initial AWS environment in a few clicks. …
AWS Best Practices: five key approaches - Cloud Academy AWS Best Practices: secure your Applications Sometimes it is better to explain a concept with a picture or diagram rather than with words. The diagram below could be a small scale deployment on AWS. You have a Web Server, an App Server, and a DB server. You should allow access from the outside world only where necessary.
9 AWS Security Best Practices - Alert Logic 9 AWS Security Best Practices 1. Become Acquainted with the AWS Well-Architected Framework While AWS isn't responsible for the security in your cloud environment, they do offer ample resources to help you protect your AWS workloads. If you're new to building on AWS, one of the first things you should read is the Well-Architected Framework.
Best practices for managing AWS access keys For more information about best practices for AWS account security, see the following resources: IAM Best Practices contains suggestions that help you secure your AWS resources with the AWS Identity and Access Management (IAM) service. The following topics provide guidance when you set up the AWS SDKs and the AWS CLI to use access keys: ...
PDF AWS Glue Best Practices: Building a Secure and Reliable Data Pipeline ... AWS Glue Best Practices: Building a Performant and Cost Optimized Data Pipeline. Are you Well-Architected? The AWS Well-Architected Framework helps you understand the pros and cons of the decisions you make when building systems in the cloud. The six pillars of the Framework allow you to learn architectural best
Top 9 Best Practices for AWS ECS Security Best-Practices for AWS Fargate. AWS Fargate is a serverless service that provides the option of fully managed and abstracted infrastructure for containerized applications managed using AWS ECS. The AWS Fargate service performs tasks such as provisioning, management and security of the underlying container infrastructure while users simply ...
Security best practices in IAM - AWS Identity and Access … Jul 14, 2022 · Use the root user to complete the tasks that only the root user can perform. For the complete list of these tasks, see Tasks that require root user credentials in the AWS General Reference. For more information, see Best practices to protect your account's root user in the AWS Account Management User Guide.
21 AWS Security Groups Best Practices | McAfee Blog Download to learn about the AWS adoption trends, security challenges and best practices around AWS and applications deployed in AWS. Download Now 6) Outbound access: Restrict outbound access from ports to required entities only, such as specific ports or specific destinations.
Getting Started: Follow Security Best Practices as You Configure Your ... Following security best practices can help prevent your root account from being compromised, which is an important safeguard because your root account has access to all services and resources in your account. Create a strong password for your AWS resources
13 AWS Security Best Practices - Check Point Software By following this AWS security best practices checklist, it is possible to improve the security of an AWS deployment. Identify Security Requirements 1. Define and Categorize Assets in AWS: It is impossible to secure systems that you don't know exist.
Introduction - EKS Best Practices Guides - GitHub Pages Welcome to the EKS Best Practices Guides. The primary goal of this project is to offer a set of best practices for day 2 operations for Amazon EKS. We elected to publish this guidance to GitHub so we could iterate quickly, provide timely and effective recommendations for variety of concerns, and easily incorporate suggestions from the broader community.
AWS Best Practices | Wharton Knowledge Base Account users can create their own roles and request that users be assigned to the roles. User Authentication Wharton strongly recommends that users authenticate with Pennkey whenever possible. Pennkey authentication ensures that users who no longer have active Pennkeys cannot access AWS linked accounts.
AWS Security Best Practices Checklist | CDWG By setting a schedule and creating regular backups, you can ensure a minimal loss of information and get back up and running as quickly as possible. 6. Create a Company Culture of Security While somewhat more abstract than other practices, creating a company culture of security is imperative to getting the most out of your AWS security services.
21 Best Practices for AWS Cloud Security - Towards Data Science Best Practices for AWS Cloud Security 1. Put your strategy first and determine if it supports various tools and controls. There's a lot of debate around whether you should put tools and controls in place first, or set up the security strategy. While it might seem like an underlying discussion, the answer is more complex.
Best practices for setting up Amazon Macie with AWS Organizations In this post, we'll walk through the best practices to implement before you enable Amazon Macie across all of your AWS accounts within AWS Organizations.. Amazon Macie is a data classification and data protection service that uses machine learning and pattern matching to help secure your critical data in AWS. To do this, Macie first automatically provides an inventory of Amazon Simple ...
PDF AWS Security Best Practices Amazon Web Services AWS Security Best Practices Page 2 Know the AWS Shared Responsibility Model Amazon Web Services provides a secure global infrastructure and services in the cloud. You can build your systems using AWS as the foundation, and architect an ISMS that takes advantage of AWS features.











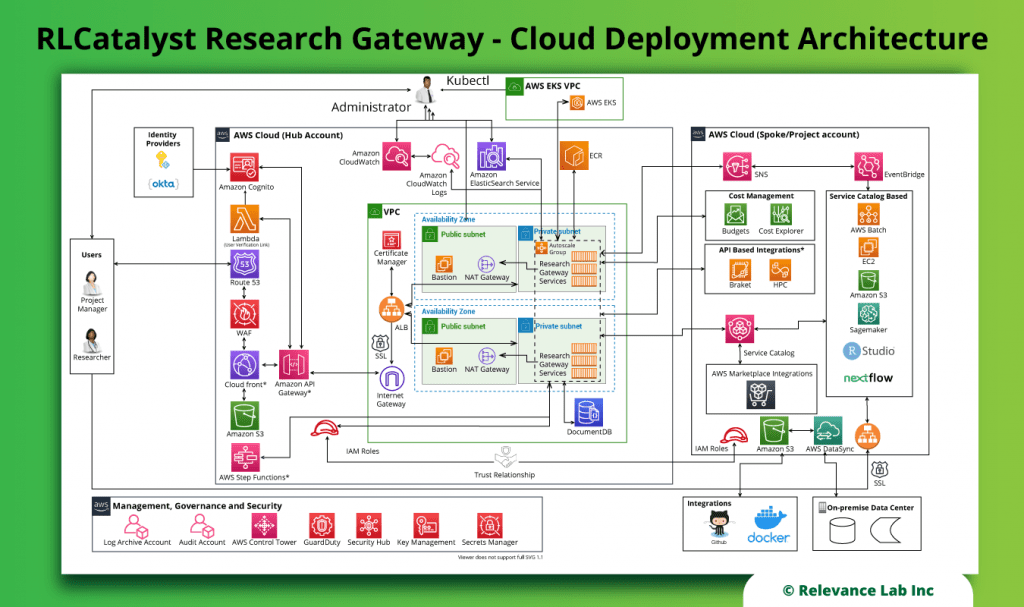
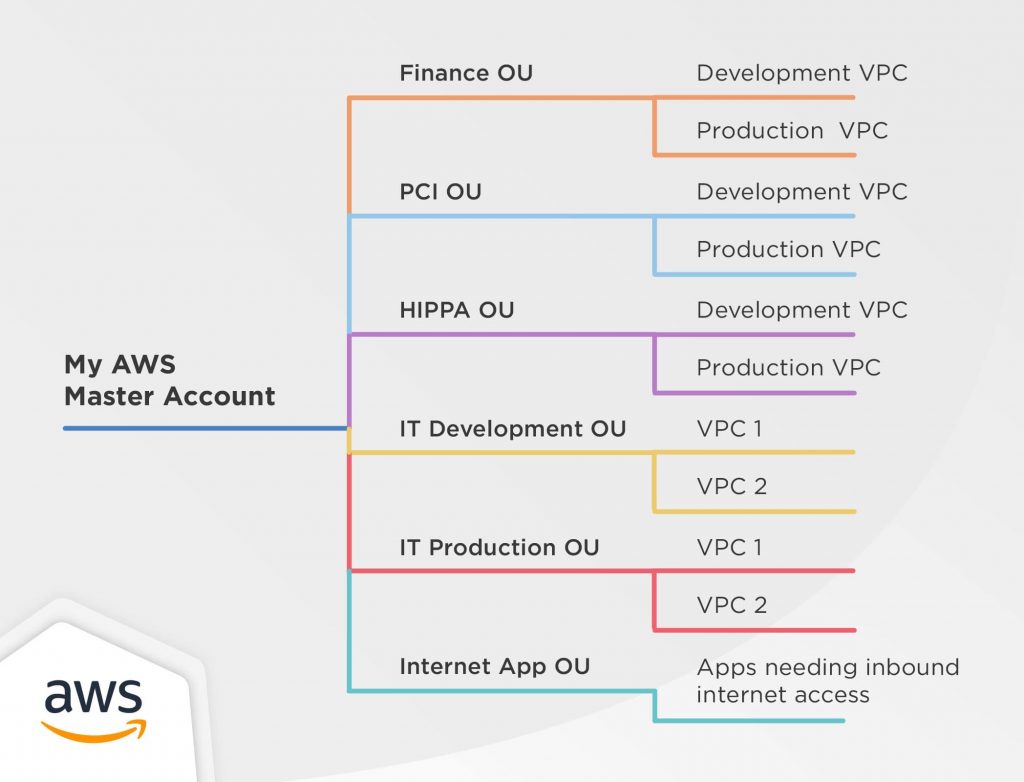


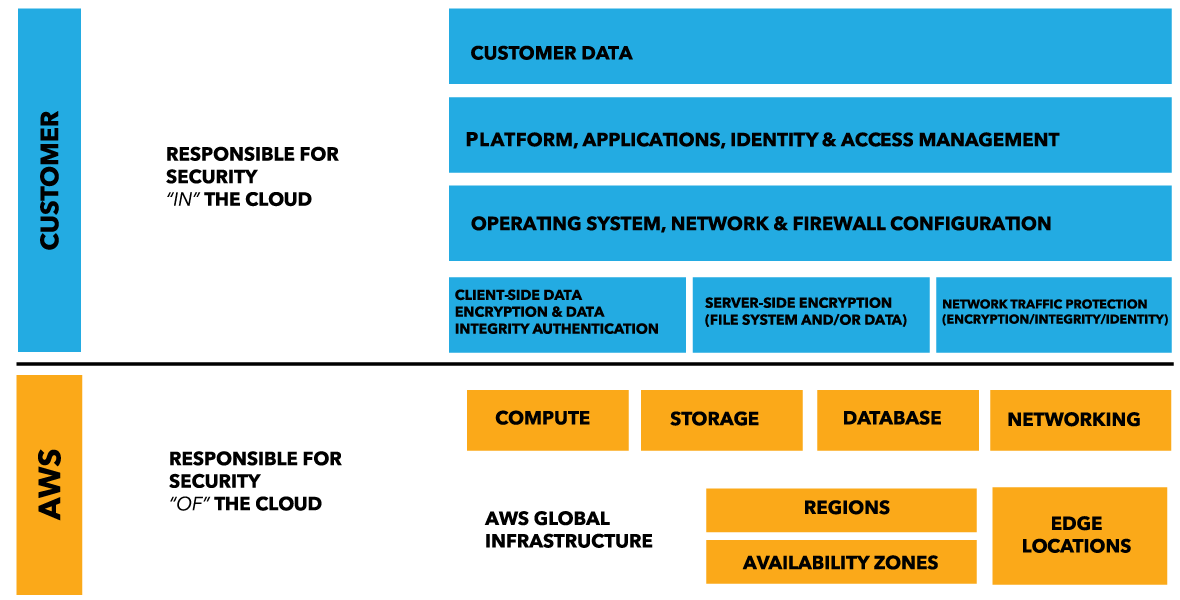
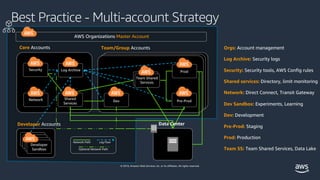










![AWS IAM: Best practices [Part 1] – DEVOPS DONE RIGHT](https://blog2opstree.files.wordpress.com/2021/03/image-36.png)




0 Response to "45 aws best practices"
Post a Comment